TLS and cookies
Key Concepts
TLS
SSL and TLS hsitory
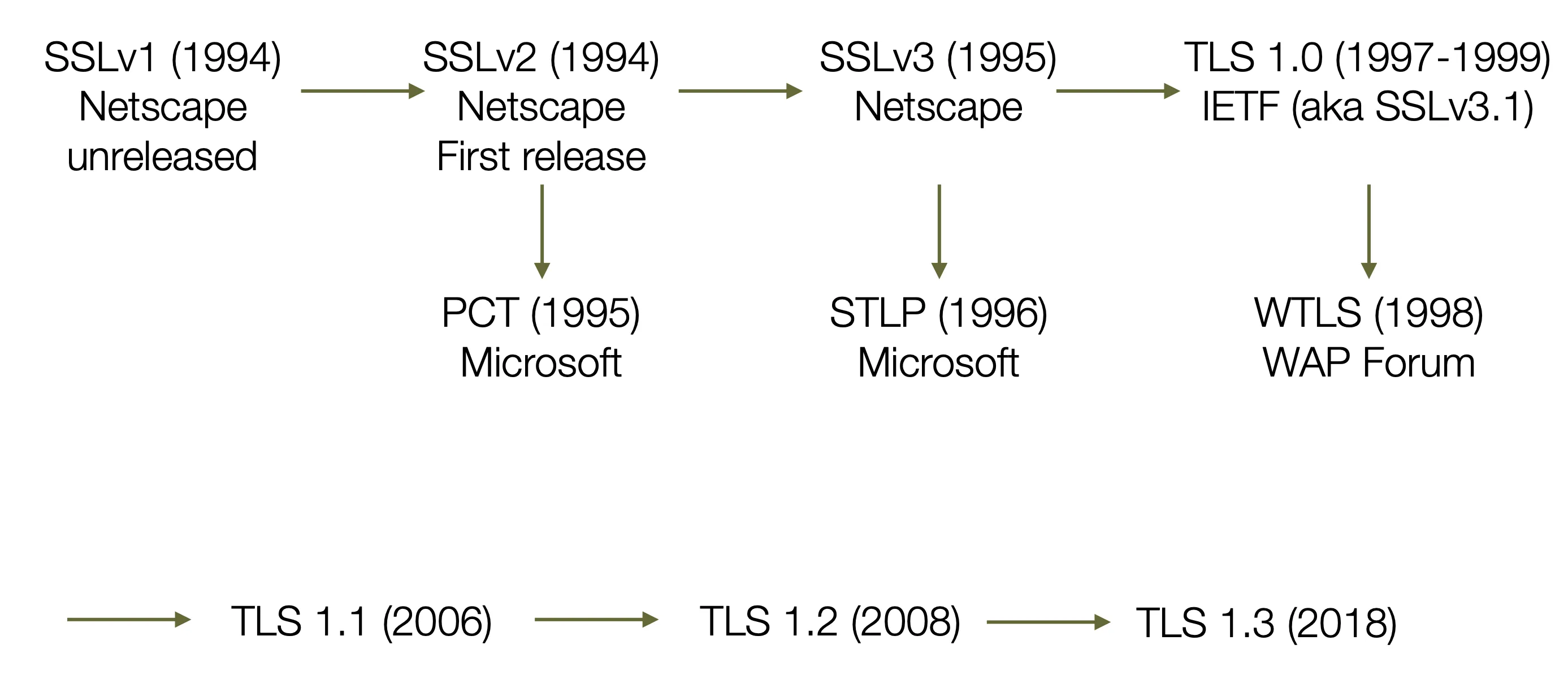
Source of image: SSL and TLS, Rescorla
SSL record structure
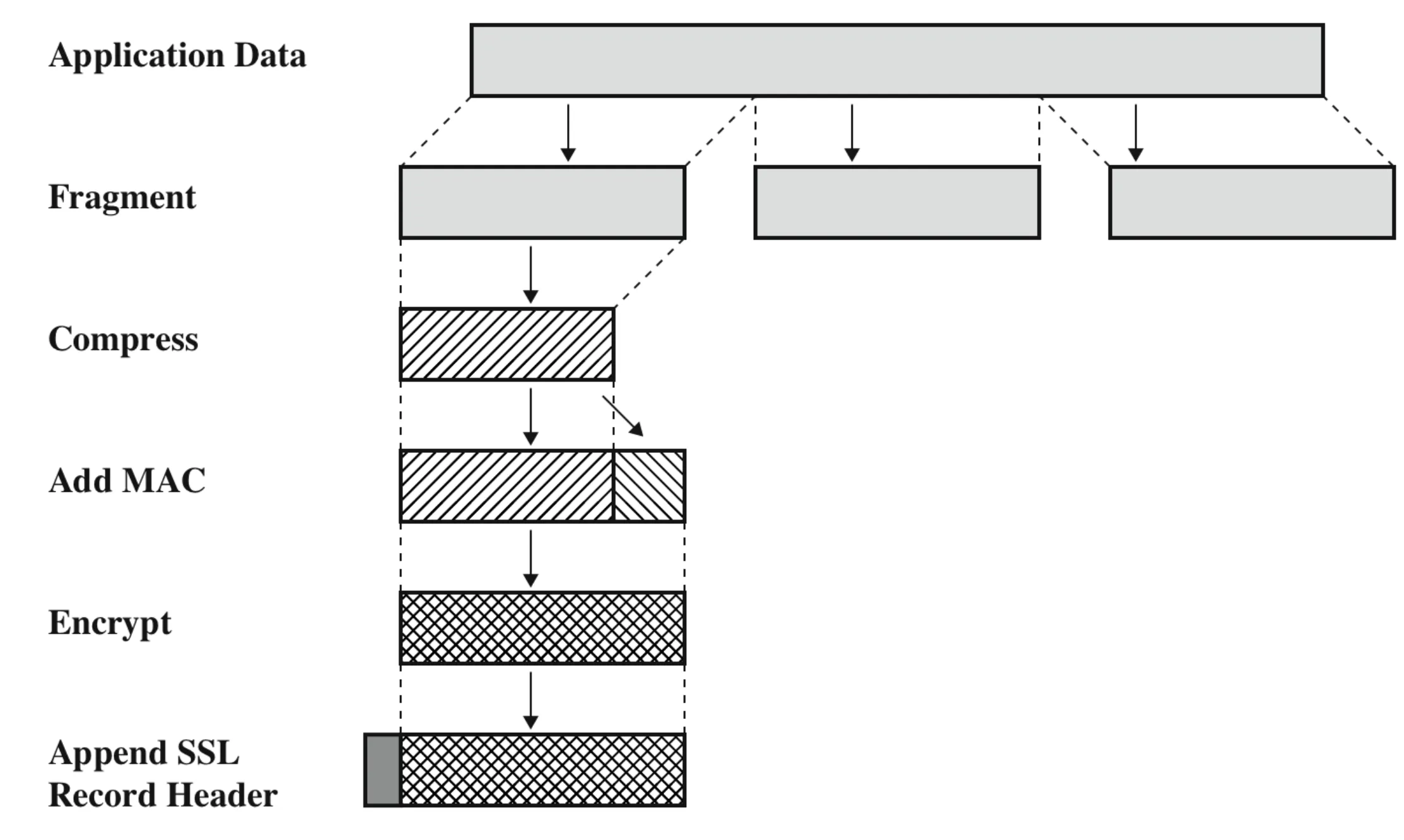
Source of image: Network and Security Essentials, Stallings
TLS handshake and DH key exchange
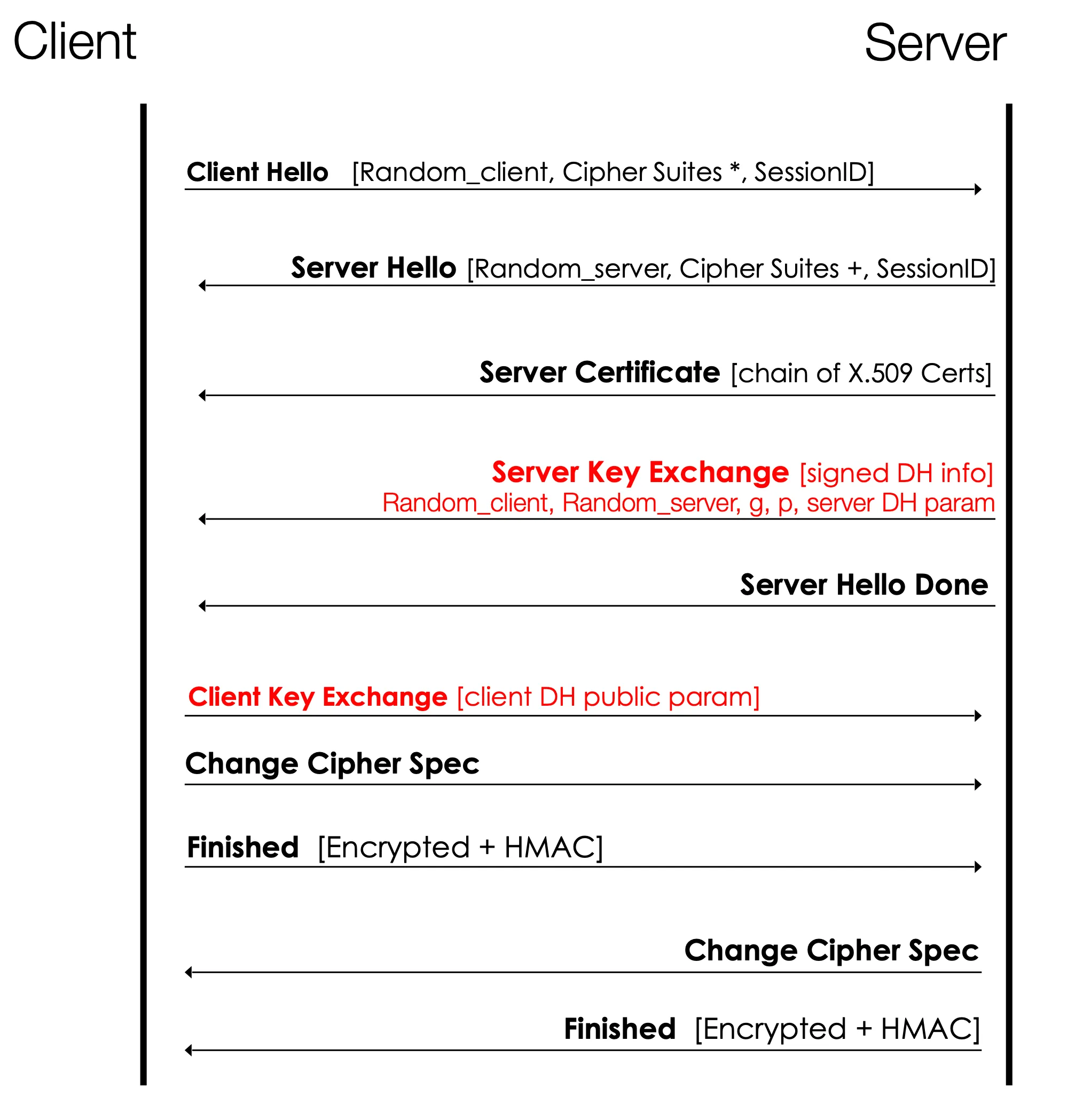
-
one of the main purpose of the TLS handshake is to etablish a shared key
- notice how everything after the key exchange is encrypted and protected with a MAC — this means an attacker cannot modify algorithms chosen
- can use a pre-shared key, meaning a key from a previous session
- Diffie-Hellman keys are ephemeral — erased after use
-
also need to authenticate the server by having it sign something
-
encryption uses authenticated encryption with a MAC
Cipher Suite
-
defines the algorithms used during the TLS connection
- key exchange algorithm — for exchanging/creating a symmetric encryption key
- authentication algorithm — for digital signatures
- bulk encryption algorithm — for encrypting the data
- MAC algorithm — for security
-
example: ECDHE-ECDSA-AES128-GCM-SHA256
- ECDHE: Elliptic-curve Diffie-Hellman — based on [elliptic curves](https://blog.cloudflare.com/a-relatively-easy-to-understand-primer-on-elliptic-curve-cryptography instead of discrete log
- ECDSA — Elliptic-curve Digital Signature Algorithm
- AES 128 — AES with 128-bit key
- GCM — Galois/Counter Mode — block cipher with high performance (parallelizable) and patent-free
- SHA256 — MAC algorithm
-
elliptic curve cryptography — higher security with shorter length keys (but not quantum safe)
HTTP cookies and DOM objects
-
Document Object Model (DOM) is a hierarchical data structure
window.document— gives you the DOMwindow.location— gives you the URL
-
cookies
- HTTP is stateless (every request is independent)
- cookies provide the state
-
cookies are
(key, value)pairs- can be stored in browser memory or persistently
- set in the
SetCookieheader
-
open the browser developer tools, network tab to examine cookies
-
important attributes
Max-AgeorExpires— controls lifetimeDomain— hosts the cookie is valid for (can’t be as broad as a TLD)Path— the file paths the cookie should be used forSecure— cookie will only be sent over HTTPSHttpOnly— only accessible over HTTP and not via DOM through JavaScript on the page