Threat modeling
Questions on the readings
The readings today are from Computer Security and the Internet, Chapter 1, sections 1.0 - 1.2, 1.4 - 1.8
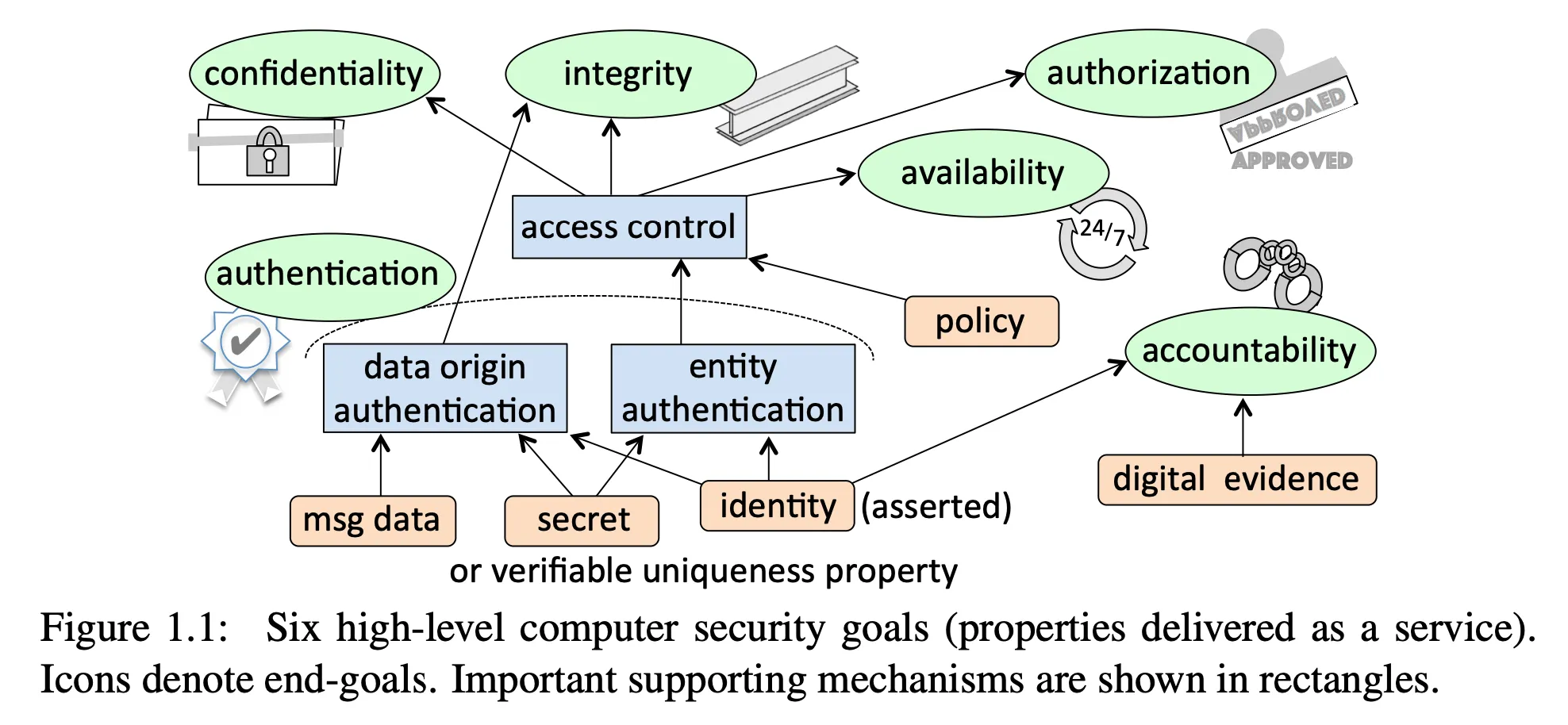
Fundamental goals of security
- Ultimate goal: Help users complete their desired task safely and without short- or long-term risk
-
CIA triad
- confidentiality
- integrity
- availability
-
AAA security
- authentication
- authorization
- accounting
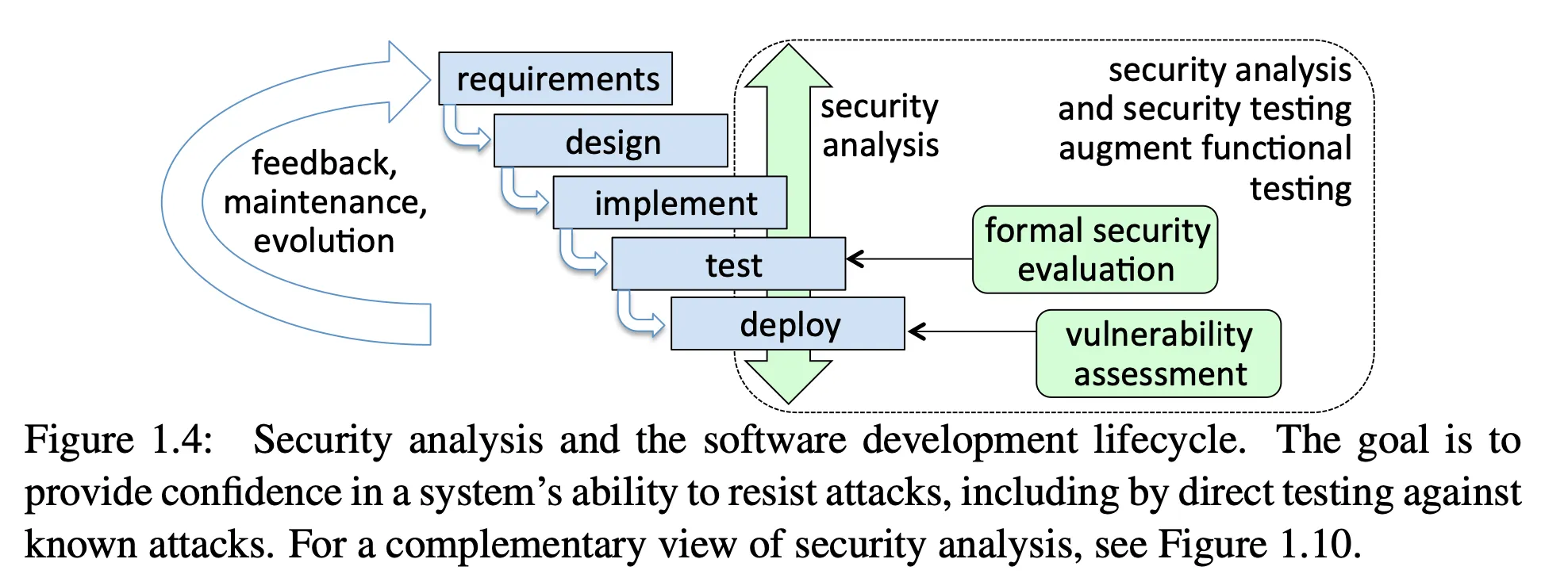
Security Analysis
- Open-ended activity to identify vulnerabilities and design defenses
Key points:
- security analysis must be done throughout the software lifecycle
- a formal security analysis can be done once a product is developed, to review against security standards (either from industry or government)
- penetration testing can be done once a product is deployed
Threat Modeling
-
Key part of a security analysis
-
wide variety of definitions
-
Book:
A threat model identifies threats, threat agents, and attack vectors that the target system considers in scope to defend against
Threat modeling is analyzing representations of a system to highlight concerns about security and privacy characteristics
Threat modeling works to identify, communicate, and understand threats and mitigations within the context of protecting something of value.
Four questions from the threat modeling manifesto:
- What are we working on?
- What can go wrong?
- What are we going to do about it?
- Did we do a good enough job?
Items included in a threat model, from OWASP:
- Description of the subject to be modeled
- Assumptions that can be checked or challenged in the future as the threat landscape changes
- Potential threats to the system
- Actions that can be taken to mitigate each threat
- A way of validating the model and threats, and verification of success of actions taken
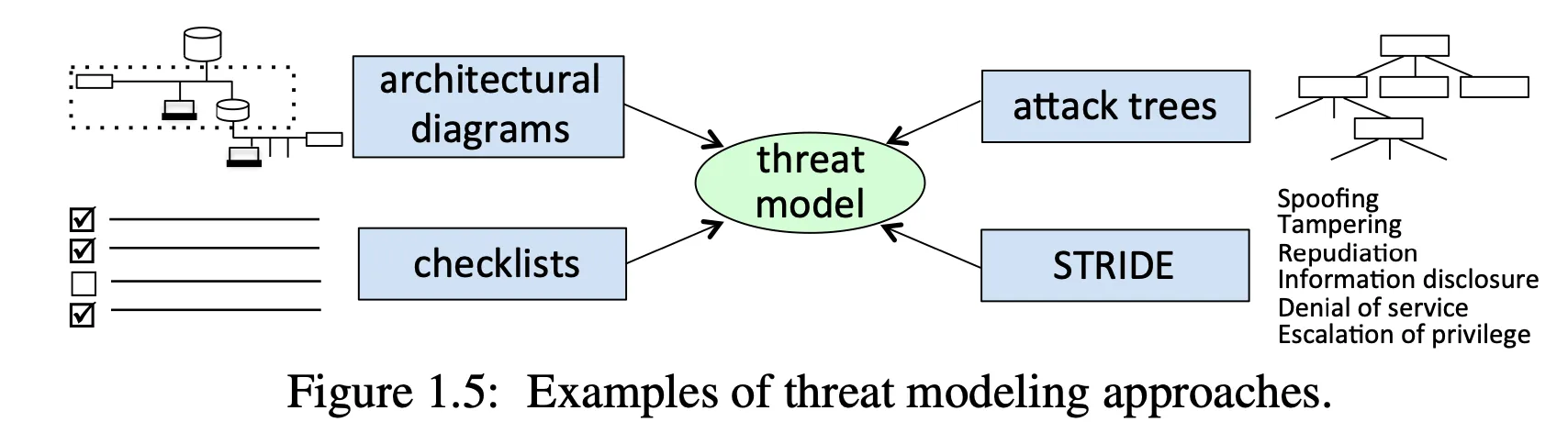
- The task of threat modeling is open-ended — long list of questions, redrawing, reconsidering
What are we working on?
-
architectural diagram of system
-
identify where information is stored in the system and how access is granted to that information
-
identify flows of control
-
example of an online banking application:
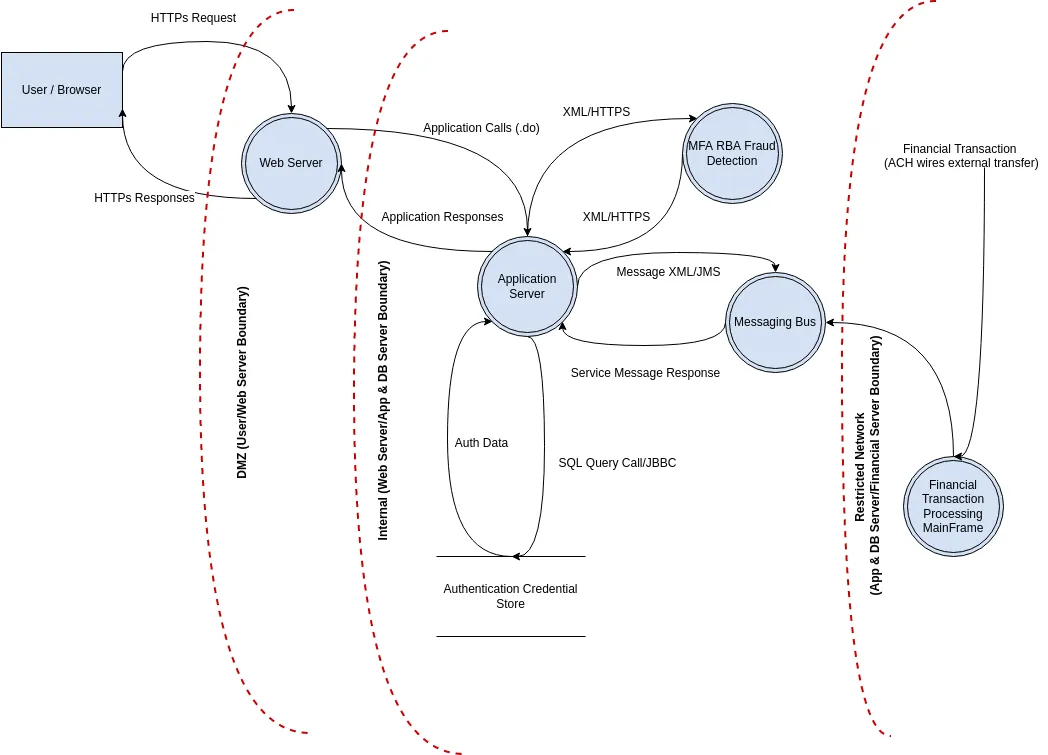
- example of password flow:
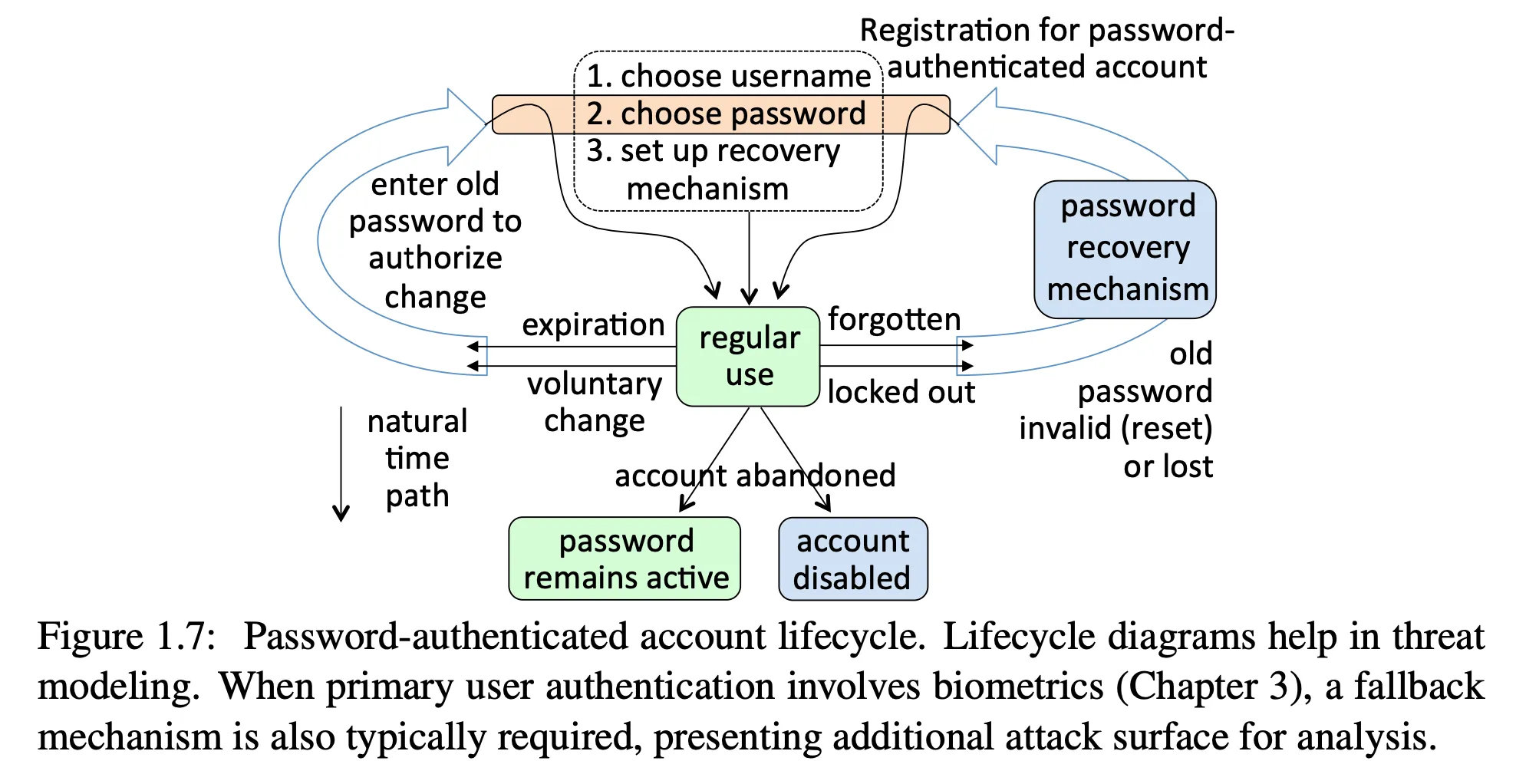
What can go wrong?
- model adversaries
- use attack taxonomies or playing cards
Modeling Adversaries
Consider:
- who are they?
- what are their objectives?
- what are their methods?
- what are their capabilities?
Examples:
- foreign intelligence
- cyber terrorists
- industrial spy
- organized crime
- crackers
- malicious insiders
- non-malicious employees
Card games
STRIDE
-
Helpful for considering possible attacks
-
Includes:
- Spoofing: attempts to impersonate a thing or an entity
- Tampering: unauthorized altering of code, data, packets, etc.
- Repudiation: denying responsibility for past actions
- Information disclosure: unauthorized release of data
- Denial of service: preventing access to services through malicious actions
- Elevation of privilege: gaining unpermitted access to resources
Enumerating Attacks
- one of the goals of a threat modeling exercise
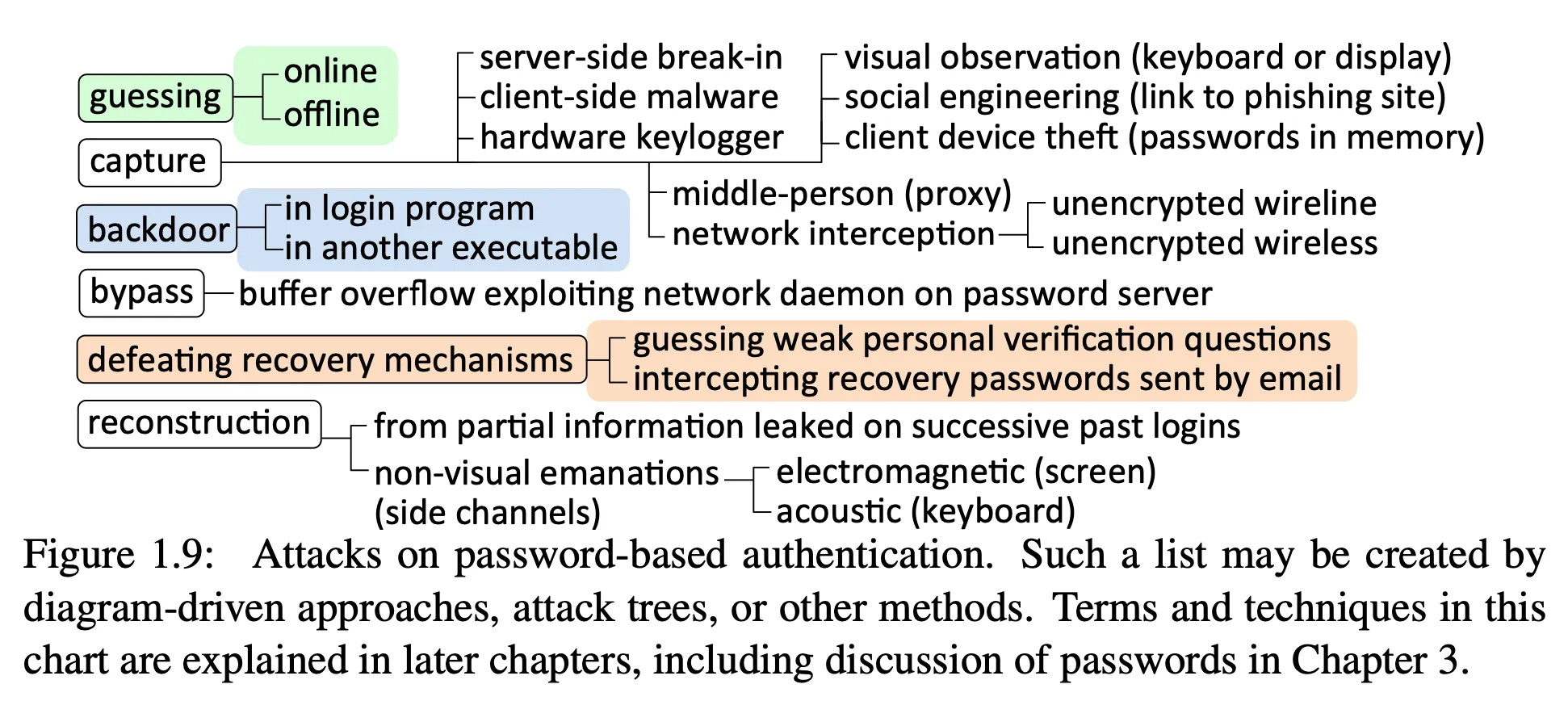
What are we going to do about it?
- Important part of a threat modeling exercise
- Want to generate a list of action items (tickets) for the organization so threats can be mitigated
Did we do a good enough job?
- Longer-term activity
- Requires metrics / measurement / logging to see if anticipated threats are stopped or new threats arise
- Can include using outside consultants
Gaps in a threat model
-
May make invalid assumptions about the system
-
Difficult to always anticipate threats
-
Example from the book:
You check into a hotel in a foreign country. You do not speak the language well. The hotel staff appears courteous, but each time you visit the lobby it seems a different face is behind the front desk. Your room has a small safe, the electronic type with its door initially open (unlocked), allowing guests at that point to choose their own combination. Upon three incorrect attempted combinations, the safe enters a lockout mode requiring hotel maintenance to reset it. You choose a combination, remember it, stash your money, close the box, then go swimming.
Is your money secure? The natural assumption is that a thief, trying to open the lock by guessing your combination, will with high probability guess wrong three times, leaving your money safe inside.
But, do you trust the hotel staff? Someone in maintenance must know the reset or master combination to allow for hotel guests who either forget their combination or enter three wrong tries. If you return and the money is gone, do you trust the hotel maintenance staff to help you investigate? Can you trust the hotel management? And the local police—are they related to hotel staff or the owner? (What implicit assumptions have you made?)
-
Need to be sure to update threat model as adversaries, technology, system change
-
Consider Figure 1.9 again — what about a malicious browser extension?
Exercises
-
watch How to Play Cornucopia to learn more about threat modeling
-
divide into teams of 4 to 5 and build a threat model for a modern automobile that
- runs a sophisticated software system that controls all aspects of the car
- is connected at all times via a satellite system
- accepts patches over-the-air for the software system
-
for the threat model
- 10 minutes developing a system diagram
- 10 minutes identifying threats
- 10 minutes identifying countermeasures
- 15 minutes for discussion