Stack Overflows
Introductions
- introductions of two students
Questions on the readings
The readings today are from Computer Security and the Internet, Chapter 6, sections 6.3
Stack-based buffer overflow attacks
-
Stack overflow attacks are REALLY common — see CVE list
-
Understand memory layout of a process: Figure 6.3, page 166
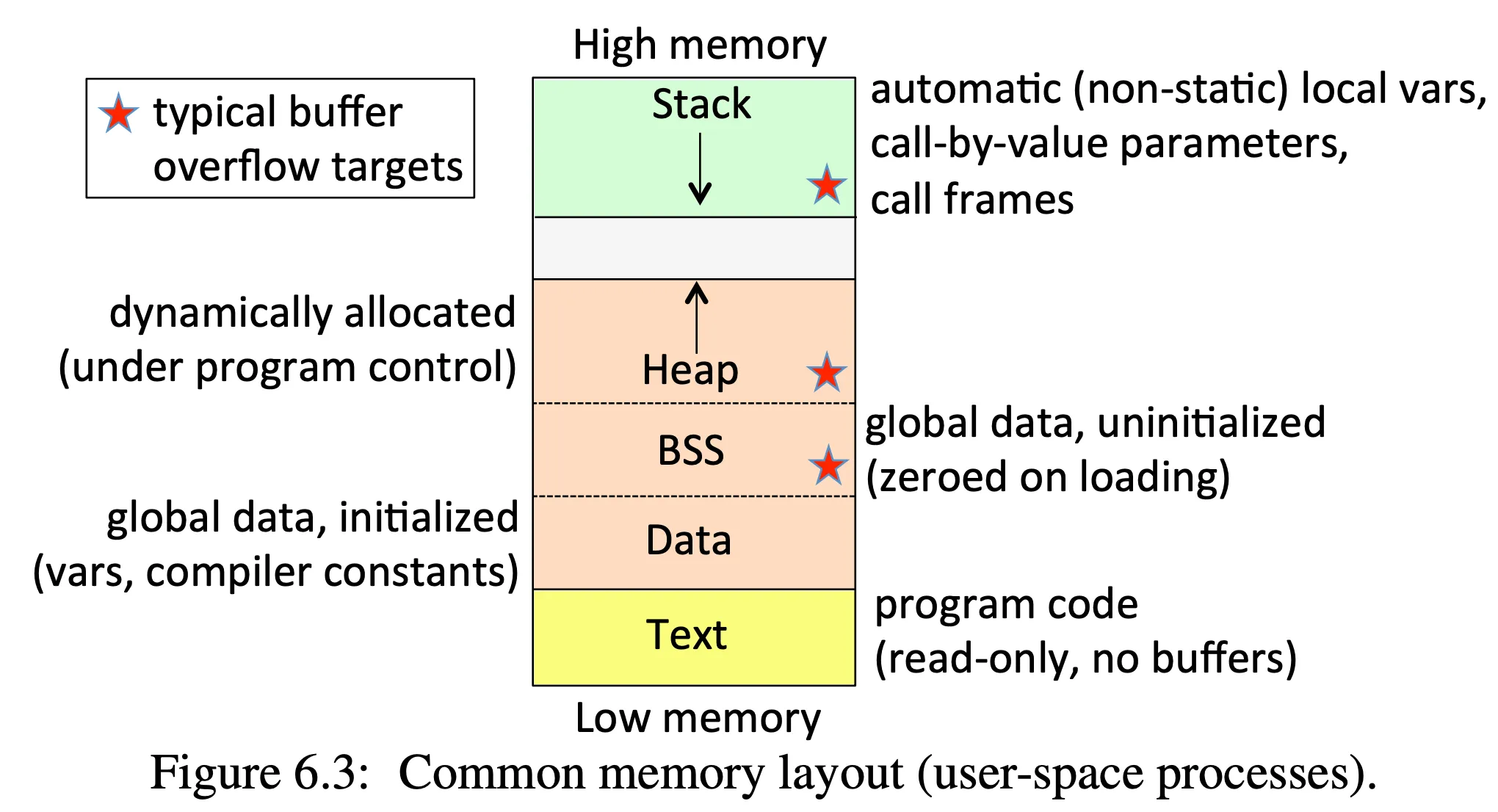
-
Data = initialized global variables
-
BSS = block starting symbol, where unitialized global memory is stored, eg. in C:
static int bufferX[4];) -
Heap = dynamically allocated memory, e.g. in C using
malloc() -
Stack = memory needed by the current function, e.g. parameters, local variables, return address
-
Understand how a process uses the stack: Figure 6.4, page 167
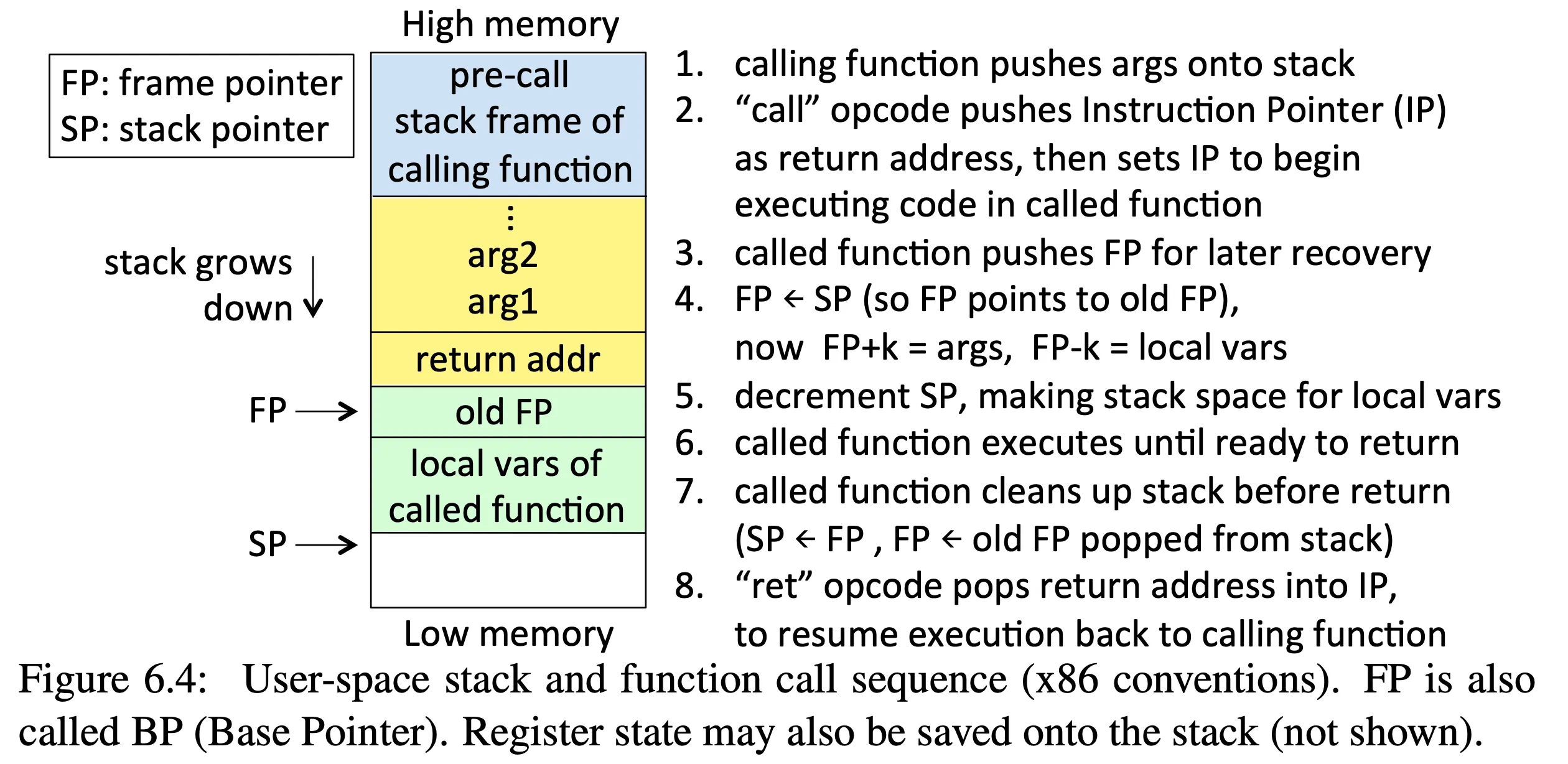
-
In a stack overflow, the attacker tries to write code to the stack and get the OS to execute it
-
Understand the basics of a buffer overflow attack: Example, Buffer Overflow, page 167, Figure 6.5, page 168
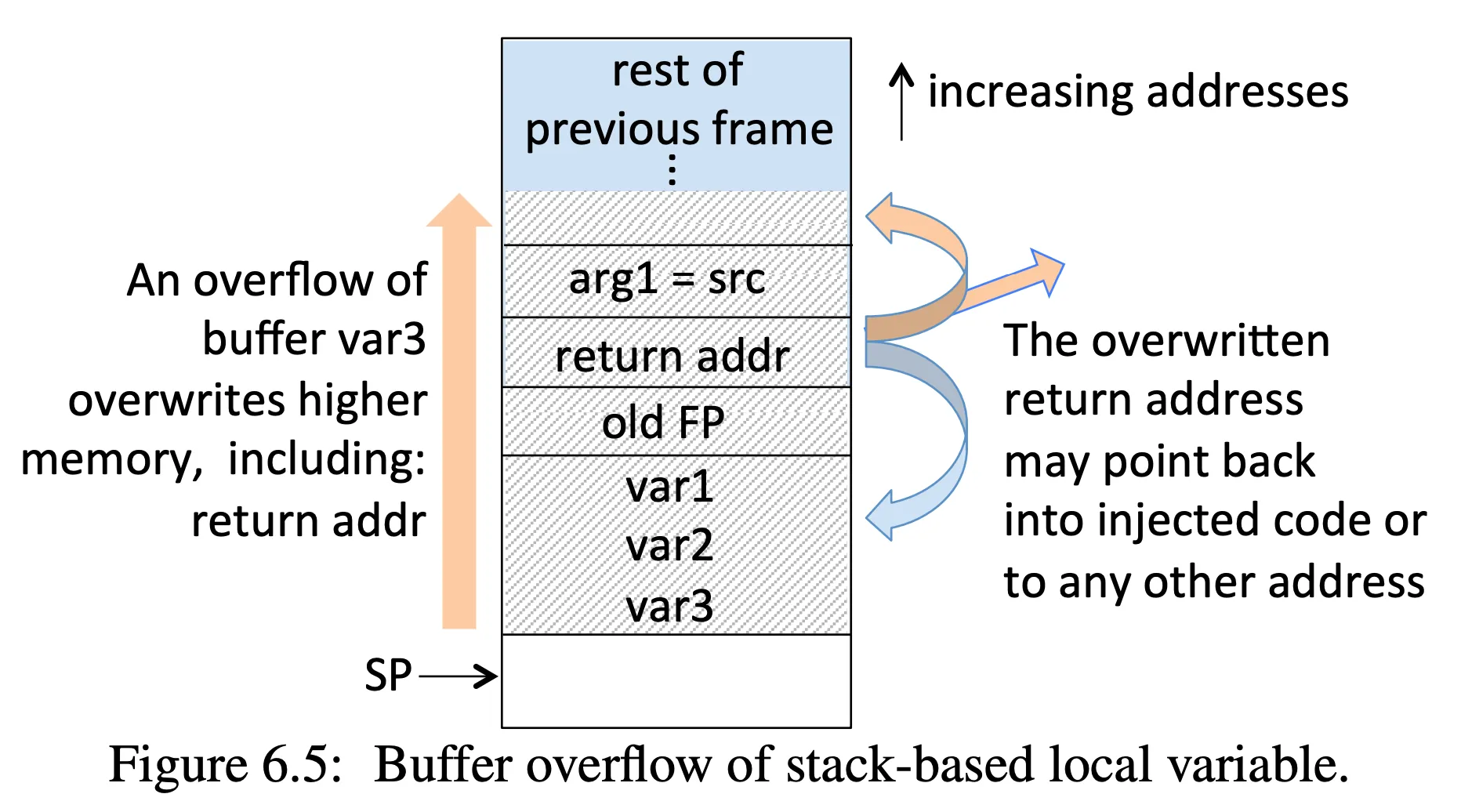
- Note, this example assumes 4-byte memory words, but it works regardless of word size
void myfunction(char *src) { /* src is a ptr to a char string */ int var1, var2; /* 1 stack word used per integer */ char var3[4]; /* also 1 word for 4-byte buffer */ strcpy(var3, src); /* template: strcpy(dst, src) */}Class exercises
See the software security repo for code we will use:
- In
buffer-overflowwe will runstack, which has an buffer overflow problem. We’ll use theexploit.pyscript to help create the overflow and direct the program to a return address of our choosing. This code implements the toy example from the book.
Time permitting, we will also try the buffer overflow 0 and buffer overflow
exploits on the
PicoCTF website.