Public Key Cryptography
Introductions
- introductions of two students
Questions on the readings
The readings today are from Computer Security and the Internet, Chapter 2, sections 2.3, 2.4
Public Key Cryptography
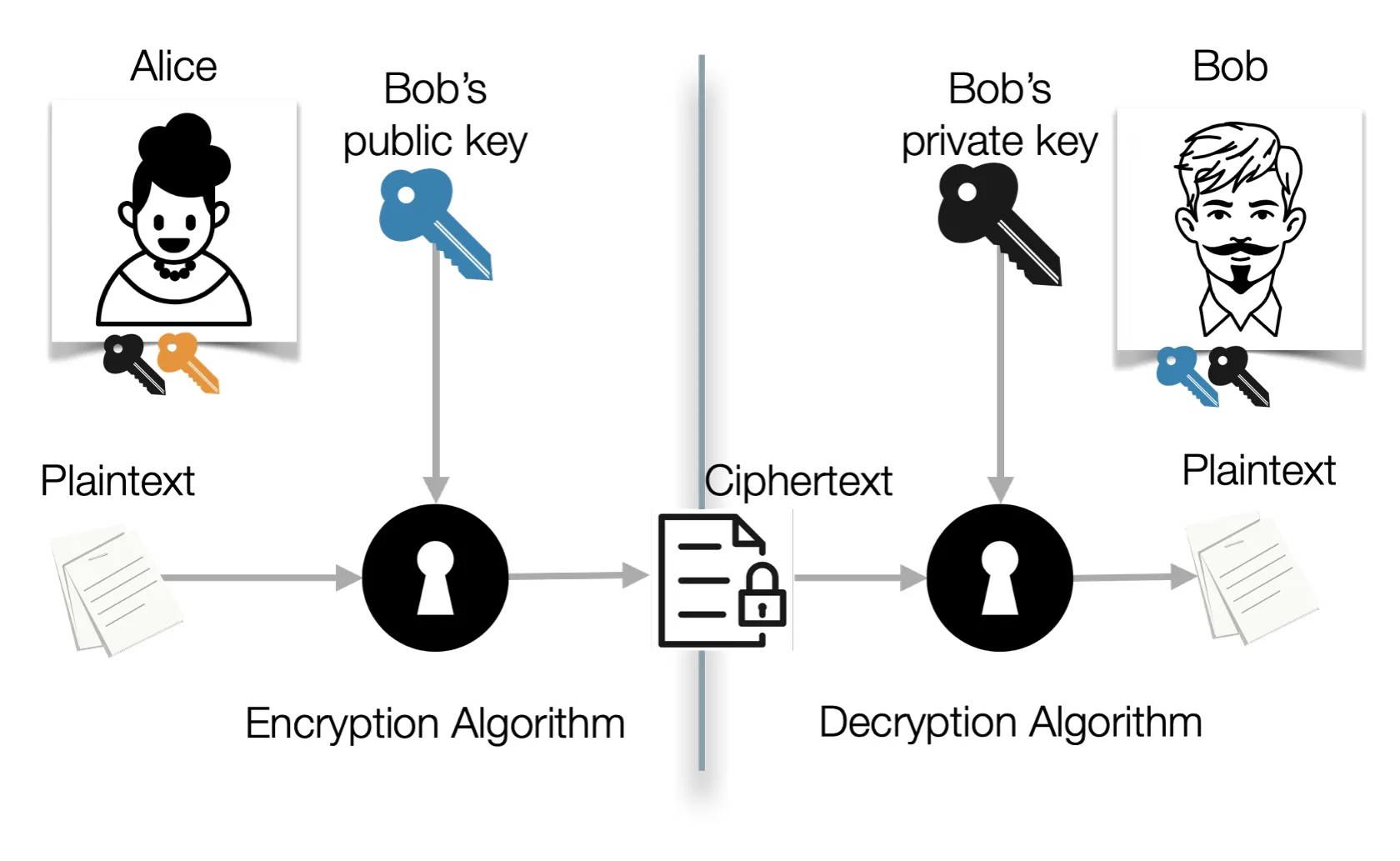
- Each party creates a separate key pair, (public key, private key). These are also called the encryption key and decryption key.
- If Alice knows Bob’s public key, she can encrypt a message using his public
key (eB) and only Bob can decrypt the message using his private key
(dB).
- c = EeB(m)
- m = DdB(c)
- Bob must keep his private key secret, otherwise anybody could decrypt private messages sent to him.
- Standard public key cryptography algorithm is called RSA — provides computational security
- Typically use padding with RSA to turn a deterministic encryption into one that incorporates some randomness. A common standard is PKCS#1 v2.
Hybrid Encryption
Usually, we use public key cryptography to bootstrap a shared, symmetric key. This is because encrypting and decrypting with a symmetric key is much faster than encrypting and decrypting with public key cryptography.
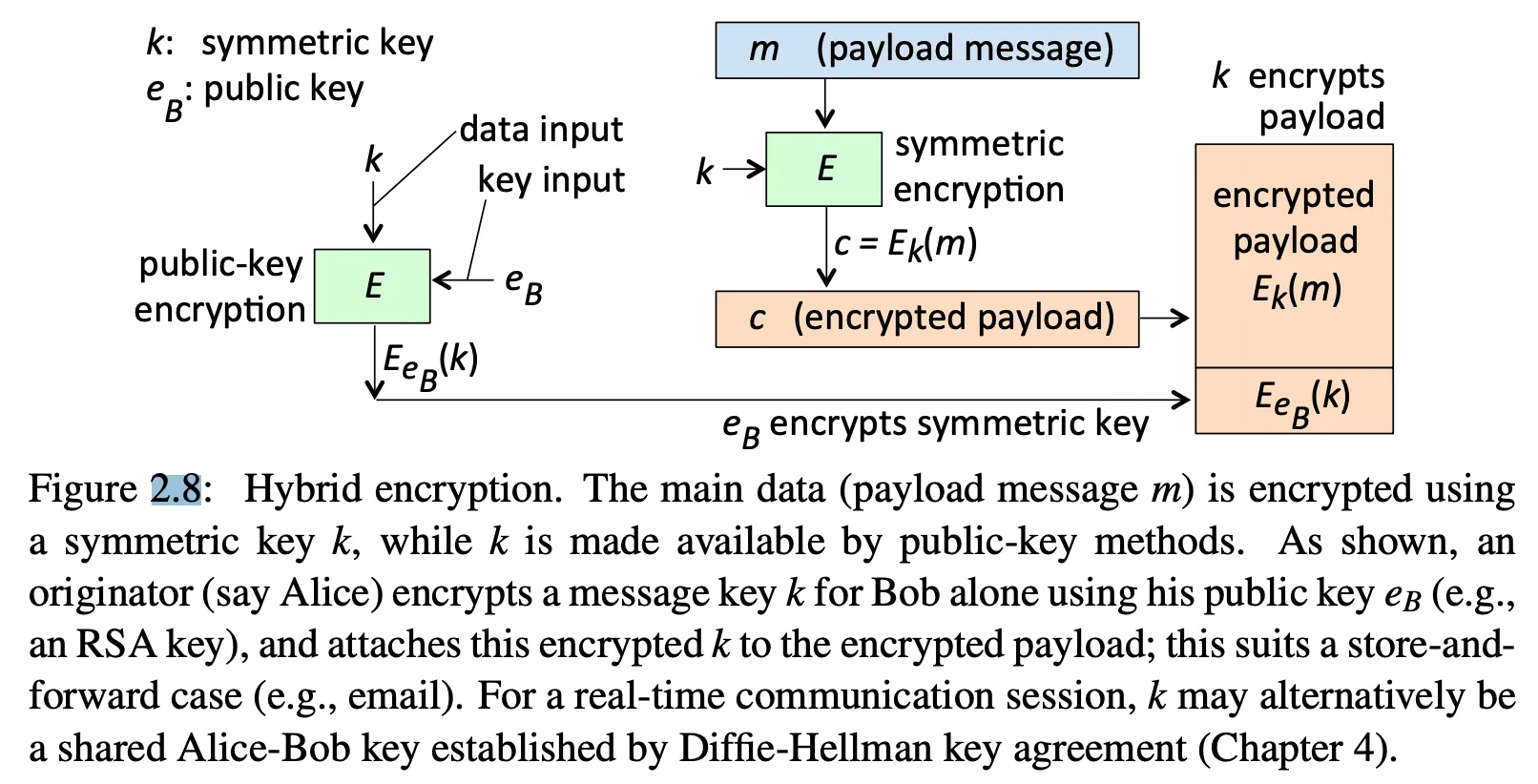
- Alice chooses a symmetric key, then encrypts it with Bob’s public key and sends it to him. Now they both have a symmetric key they can use to encrypt and decrypt messages to each other.
- Alice and Bob typically choose a new symmetric key each time they communicate, so we call this a session key.
Digital Signatures
We can also use public key cryptography to implement digital signatures. Here, private key is used to sign and the public key is used to verify. Note that signing uses encryption and verifying uses decryption.
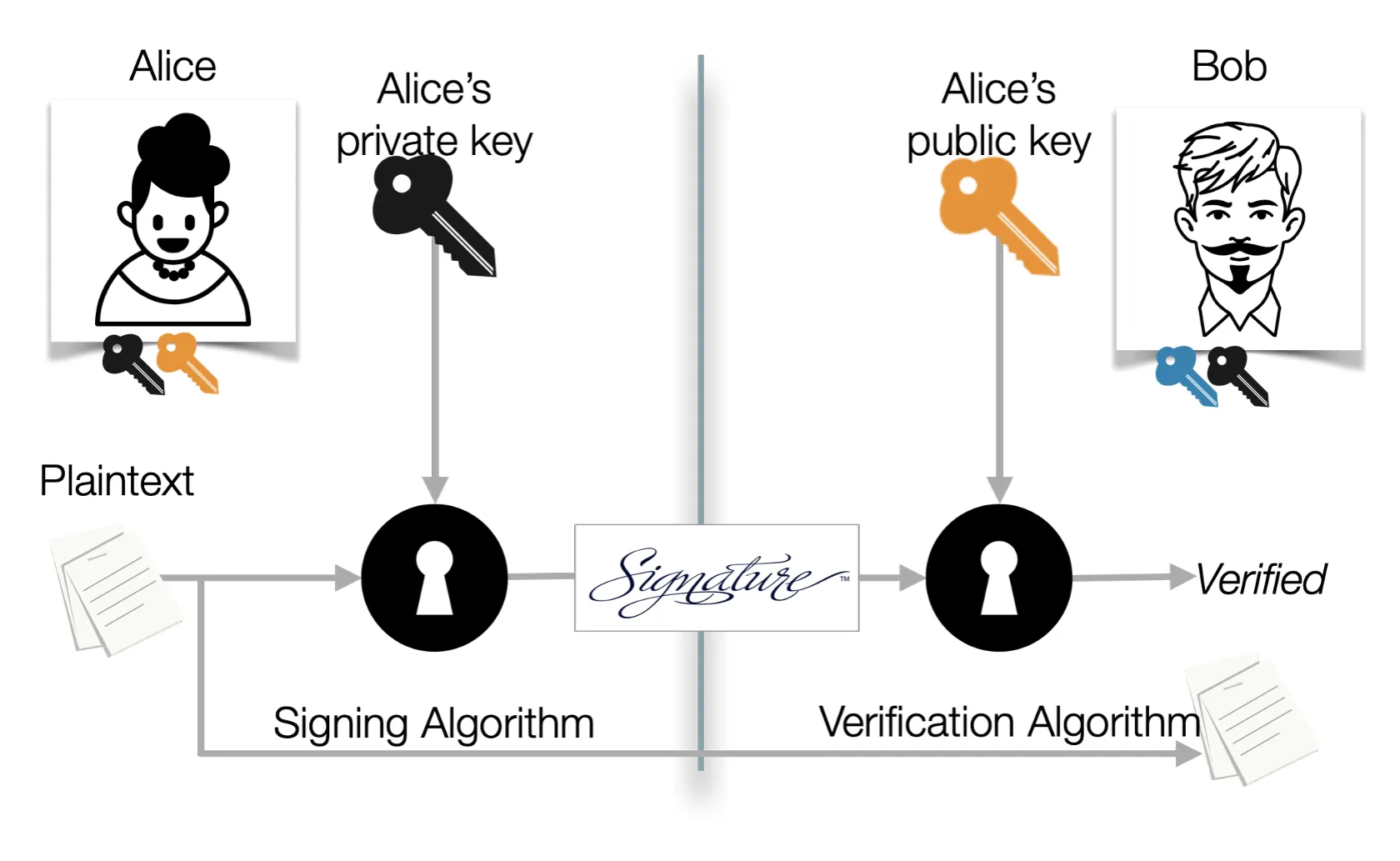
- Alice signs (encrypts) a message with her private key (sA). Bob can verify (decrypt) the message with Alice’s public key (vA). Here we use (v, s) to represent the (public key, private key).
- Be sure to use separate keys for encryption/decryption and signing/verifying. signing/verifying.
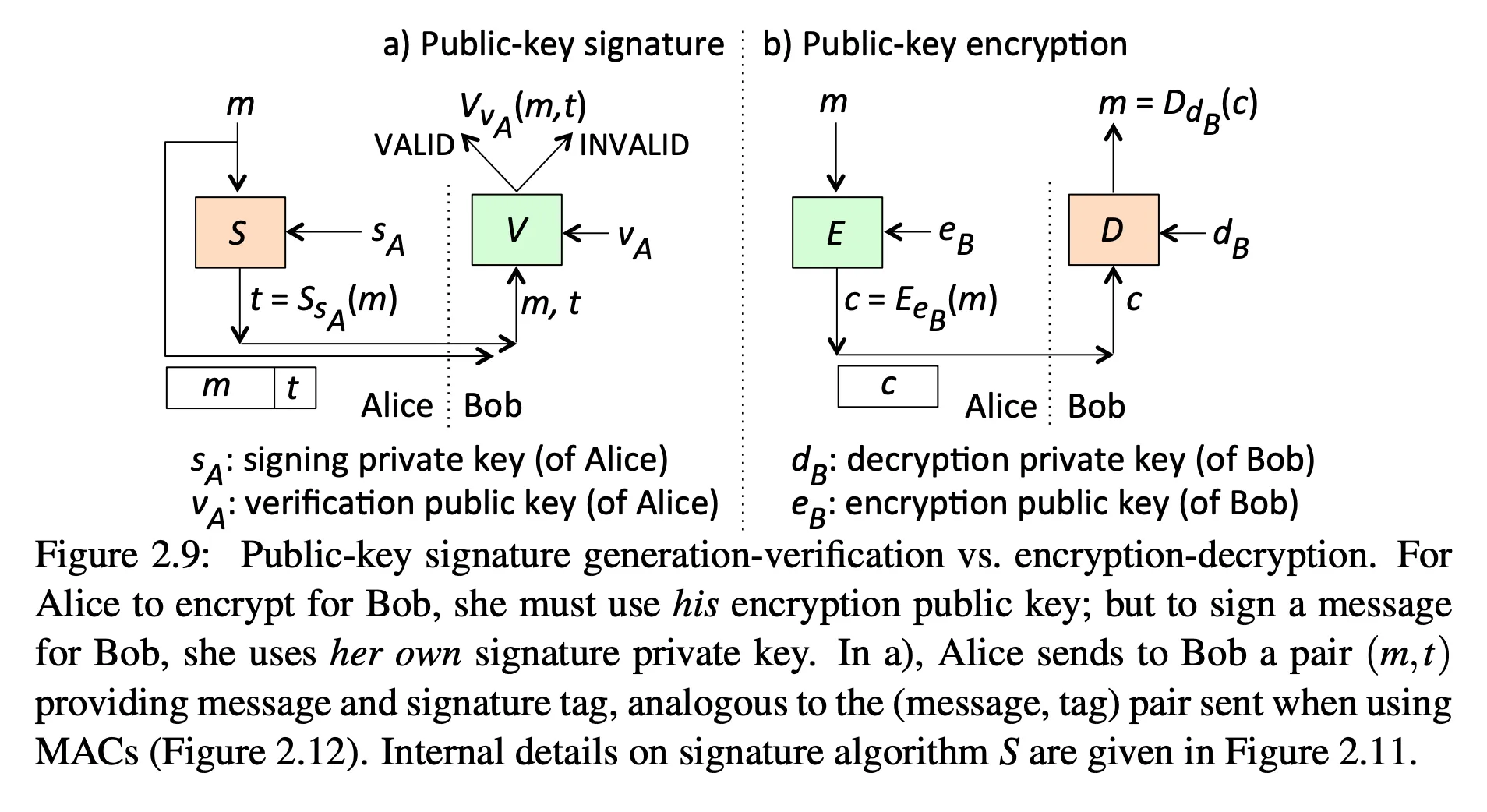
-
Digital signatures provide:
- data origin authentication — we can verify who signed the message
- data integrity — we can verify whether the message is the same as what was signed
- non repudiation — the signer can’t claim they didn’t sign the message (unless someone stole their private key)
-
Use of public key cryptography by the general public is hard because it requires you to keep your private key safe and to have a reliable way to distribute your public key to others. These are key management issues.
Hybrid encryption with integrity
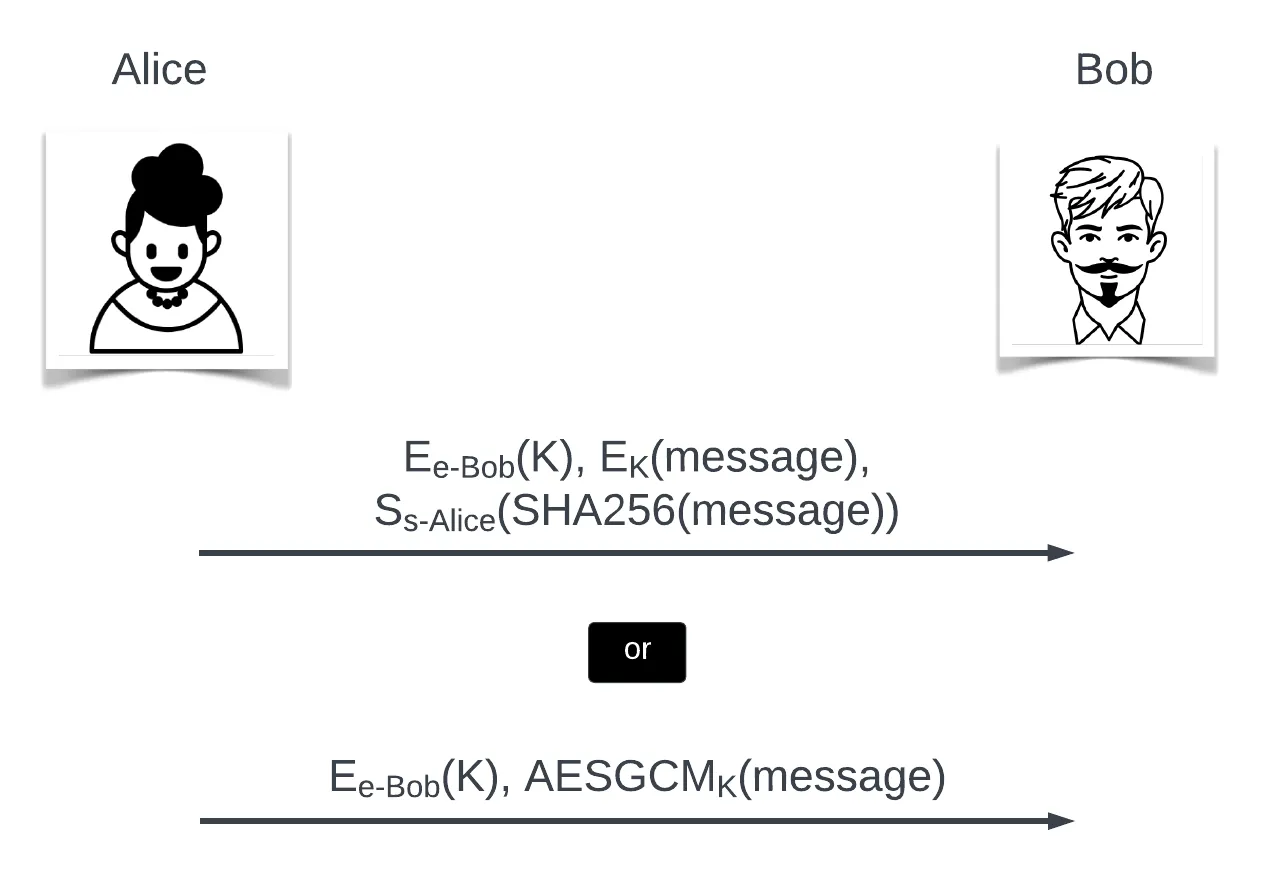
- A digital signature of a hash of the message ensures Bob knows the message came from Alice the message hasn’t been altered.
- AES with GCM provides integrity and, assuming only Alice and Bob know the symmetric key, then assures Bob that Alice sent the message.
- Getting all the pieces right is tricky. See Defective Sign & Encrypt in S/MIME, PKCS#7, MOSS, PEM, PGP, and XML. Use TLS where possible.
Extra reading
- The Marvin attack
- Stop using RSA PKCS#1 v1.5 encryption! On the TLS level, only servers that enable RSA encryption are affected. Most modern clients support the use of Elliptic Curve Diffie Hellman, thus disabling ciphersuites that use RSA encryption is the recommended way to fix this vulnerability.
Class exercises
We are using the Rust Crypto crates.
See the Rust Cryptography repo for RSA code examples.