Networking background

Internet components and structure
The Internet is:
- roughly hierarchical
- composed of networks
- composed of routers, links, a wide variety of edge devices
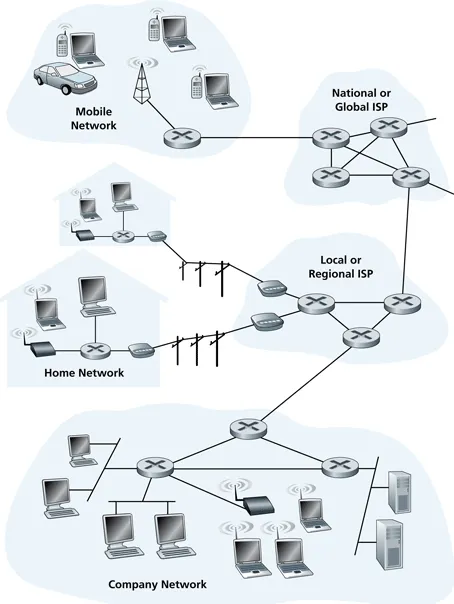
- networks connect using customer-provider relationships (usually in a contract!)
- tier-1 ISPs provide international coverage, treat each other as peers
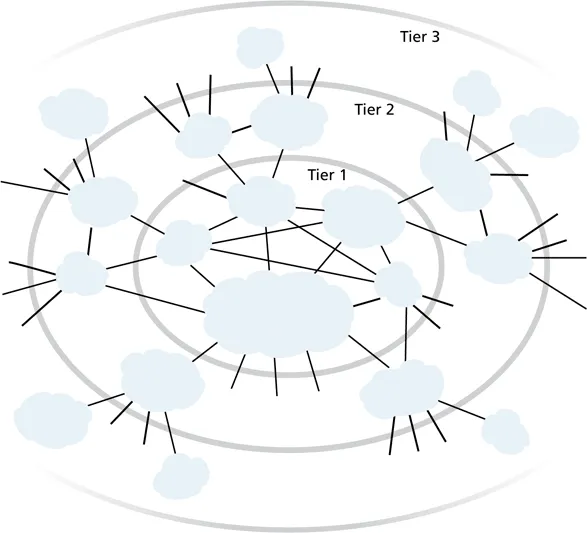
-
Lumen’s network map shows what a Tier 1 ISP looks like
-
the Internet is only roughly hierarchical, there may be many connections among peers and across levels
Internet architecture
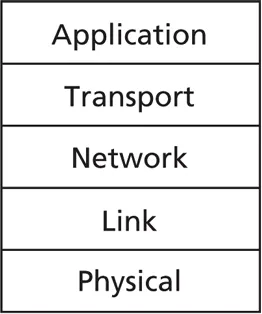
-
layering helps to build complex systems
- split large system into smaller pieces
- identify each layer’s functionality and interfaces
- can change a layer’s implementation as long as interfaces remain the same
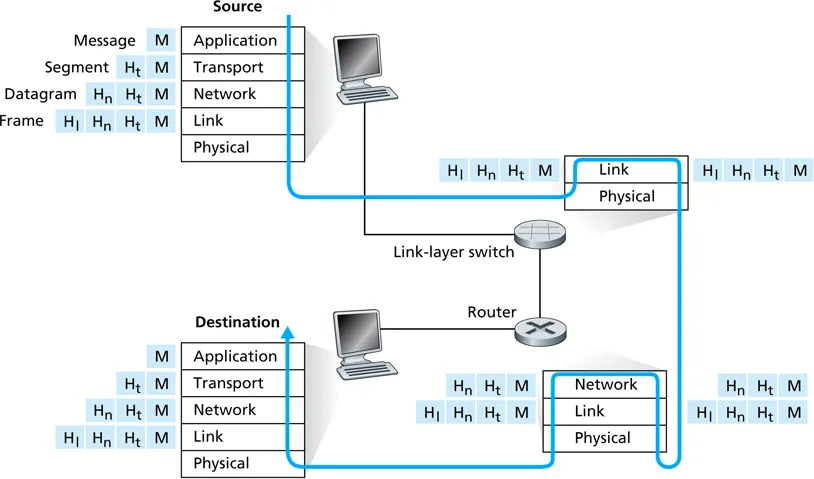
-
encapsulation is used when sending packets, decapsulation is used when receiving packets
Link layer
-
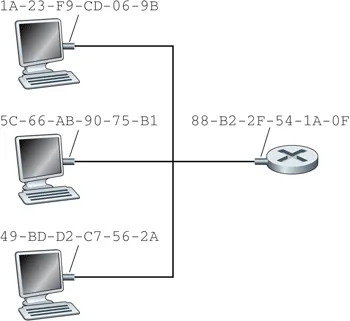
MAC addresses
- used to get frame from one interface to another physically-connected interface (on the same network)
- most are 48 bits long, depends on link-layer protocol
- address burned into the adapter ROM
- broadcast address usually all ones (FF-FF-FF-FF-FF-FF)
-
address assignment administered by IEEE
- manufacturer buys portion of MAC address space (prefix)
- uses that prefix for all MAC addresses and ensures it does not reuse the suffix
- uniqueness provides address portability
Network Layer
- IP — Internet Protocol
- simplest definition of the Internet: all the devices that speak IP
IPv4
- common protocol for all networks
- very simple
- has lasted nearly years (since ~1978!)
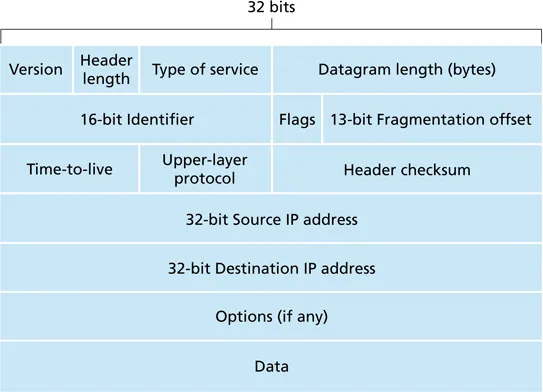
-
source IP address
-
destination IP address
-
TTL (hop count)
-
protocol: typically UDP or TCP
-
IP addresses
- 32 bits
- dotted decimal notation
byu.eduis128.187.16.184
-
forwarding process: check the destination address
- is this one of my addresses? send to next protocol specified in IP header
- is this one of my subnets? send to link layer to forward to the destination
- do I have a route? send to link layer to forward to next IP hop
- destination unknown! send an ICMP error to the source of the IP packet
IPv6
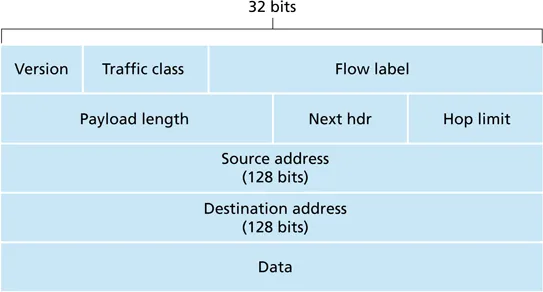
-
simplified
-
result of negotiation
-
flow label and traffic class: used to map traffic into classes of service
-
Next Header: upper layer protocol or option
-
IPv6 addresses: 128 bits
Routing Protocols
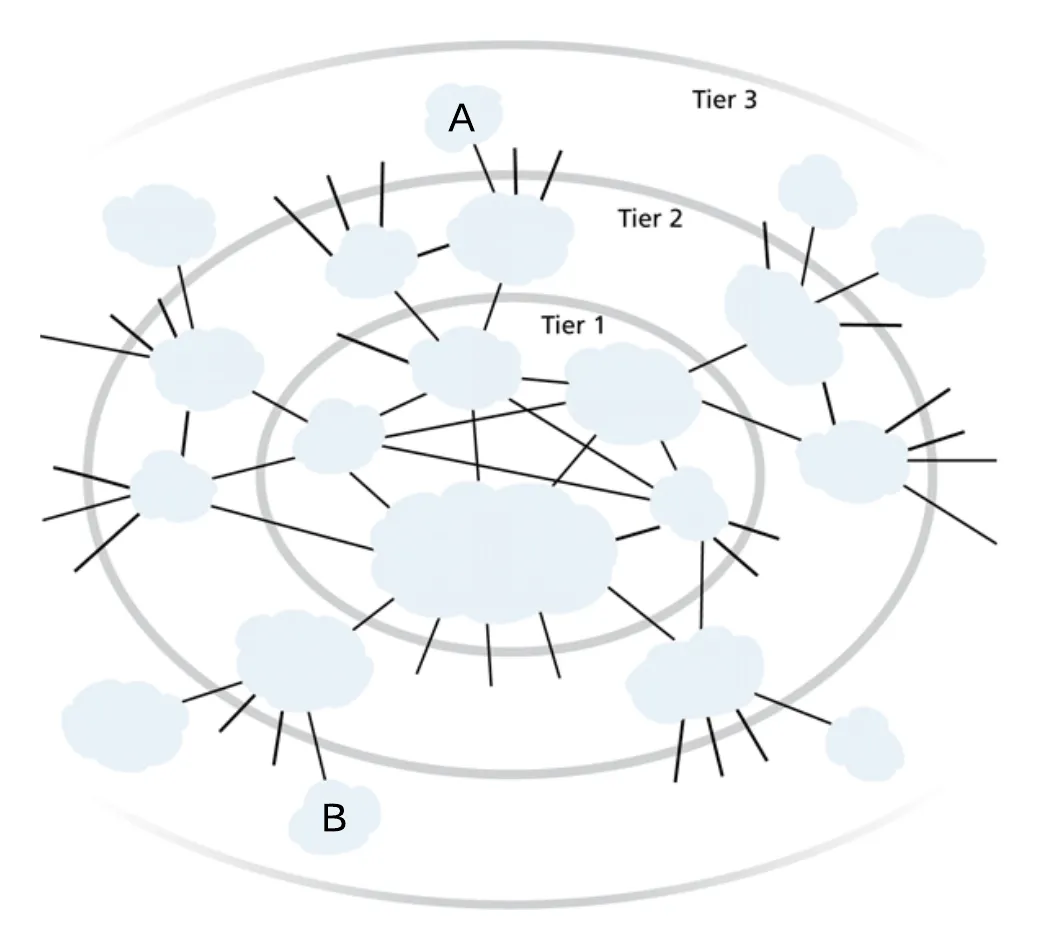
- routing protocols decide which route should a packet at A take to reach B
- different protocols for intra-network and inter-network routing — see CS 460
Transport Layer
UDP
- best-effort service
- connectionless: no state setup
- unreliable: lost packets are not re-sent • no flow control
- no congestion control (won’t slow down, you can send as much and as fast as you want)
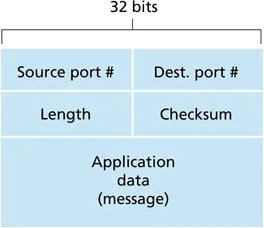
-
defined in RFC 768, from 1980
- port numbers (16 bits each)
- length of UDP segment, including header (bytes)
- checksum: detect some bit errors in transmitted segment
- application data (sometimes called ADU)
-
well-known ports: FTP (21), SSH (22), SMTP (25), HTTP (80), HTTPS (443)
-
binary protocol
TCP
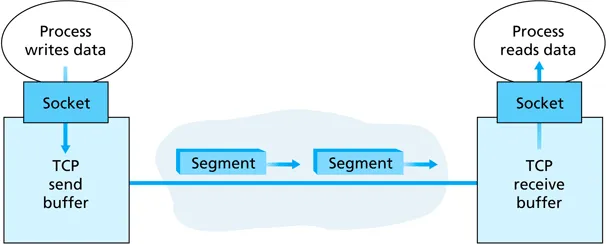
-
pipelining: multiple data segments outstanding at once
- VERY important to use the high bandwidth available on the Internet
-
TCP has two primary functions
- reliability
- congestion control
-
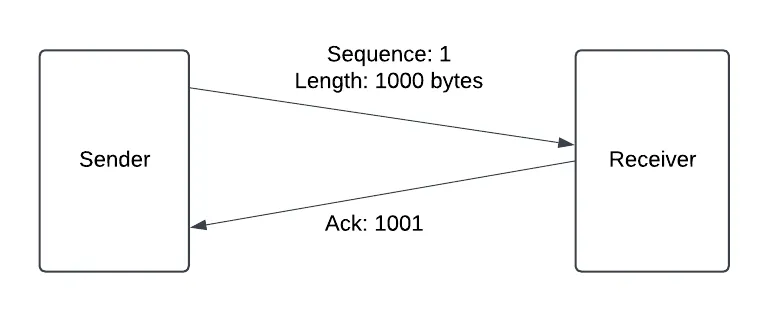
reliability
- make sure every packet gets through
- every packet gets a sequence number
- resend any packets that are dropped
-
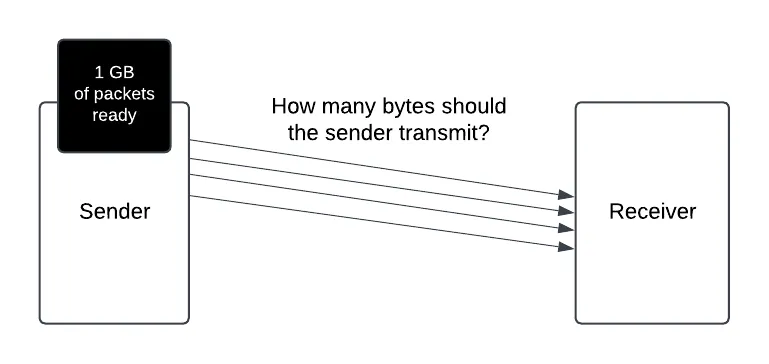
congestion control
- control the rate at which packets are sent
-
basic algorithm
- gradually increase rate
- any dropped packet means you sent too fast — slow down
- then ramp back up again
- continually probe for more bandwidth, but slow down when loss occurs
- converges over time to a fair allocation of bandwidth among competing flows
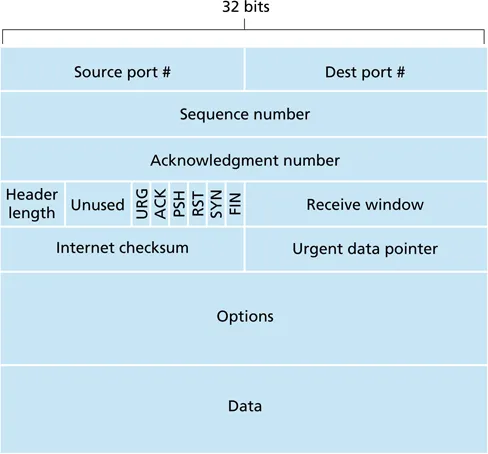
- sequence and ACK number: count in terms of bytes
- flags
A: ACK number is validR(RST): reset connectionS(SYN): establish connectionF(FIN): close connectionU(URG): urgent data, typically not usedP(PSH): push (send) data immediately, used for TELNET
- receive window: number of bytes receiver can accept (flow control)
Why is the Internet so vulnerable to attacks?
The Design Philosophy of the DARPA Internet Protocols
- fundamental goal: develop an internetwork for existing networks
- second-level goals (in order of importance)
- survivability
- multiple types of service (delay vs bandwidth, reliable vs datagram)
- variety of networks
- distributed management
- cost effective
- host attachment with low effort
- accountable resources
→ security was not considered Brief History of the Internet