Heap Overflows
Introductions
- introductions of two students
Questions on the readings
The readings today are from Computer Security and the Internet, Chapter 6, sections 6.4.
Heap-based buffer overflow attacks
- Dangerous when the heap is both writeable and executable
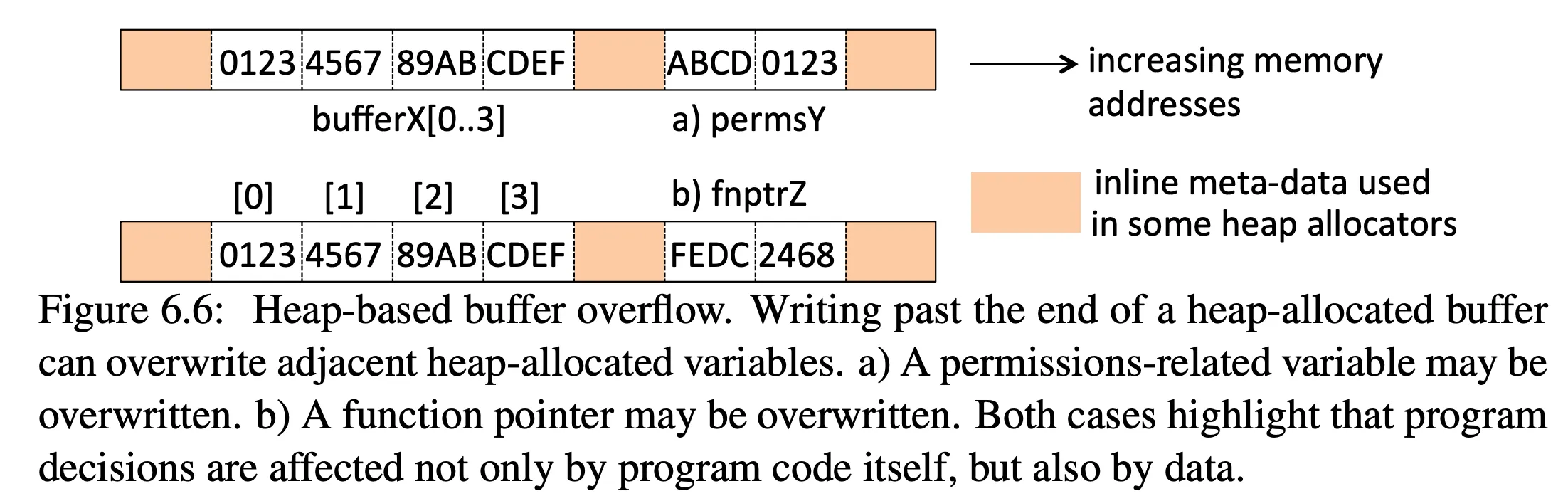
- see Figure 6.6 to understand why an attacker writing to the heap is dangerous
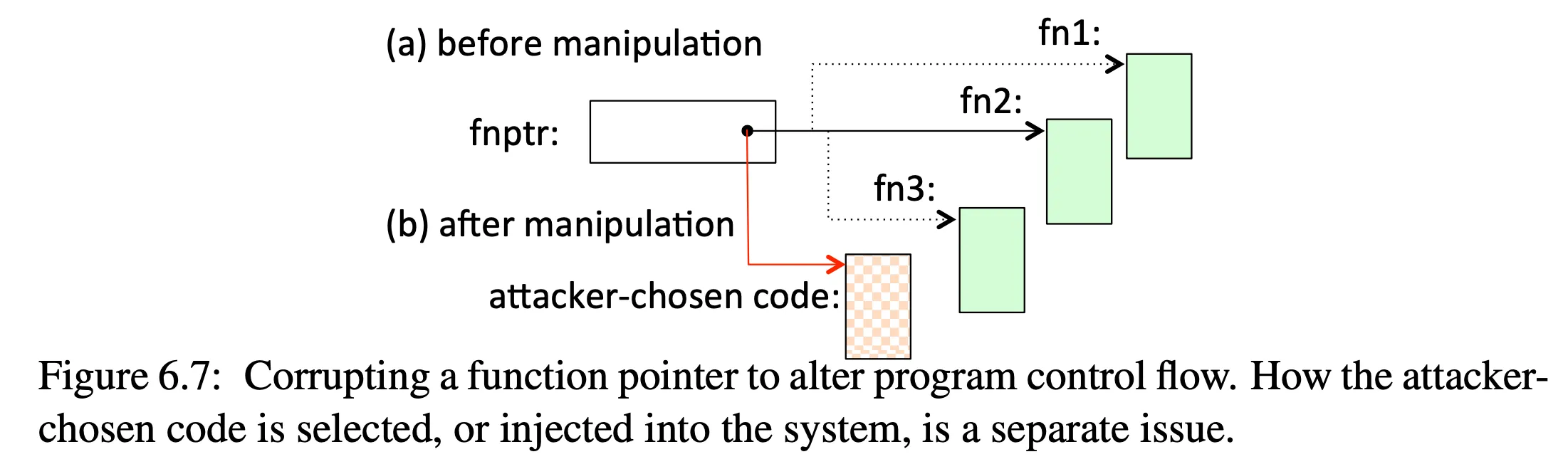
- see Figure 6.7 for an example of overwriting a function pointer:
- understand the types of state that can be corrupted
- jump table — see below
setjump— seee Wikipedia page on setjump
MyJump(int c){ switch(state) { case 0: goto func0label; case 1: goto func1label; case 2: goto func2label; }}-
understand exploit steps
-
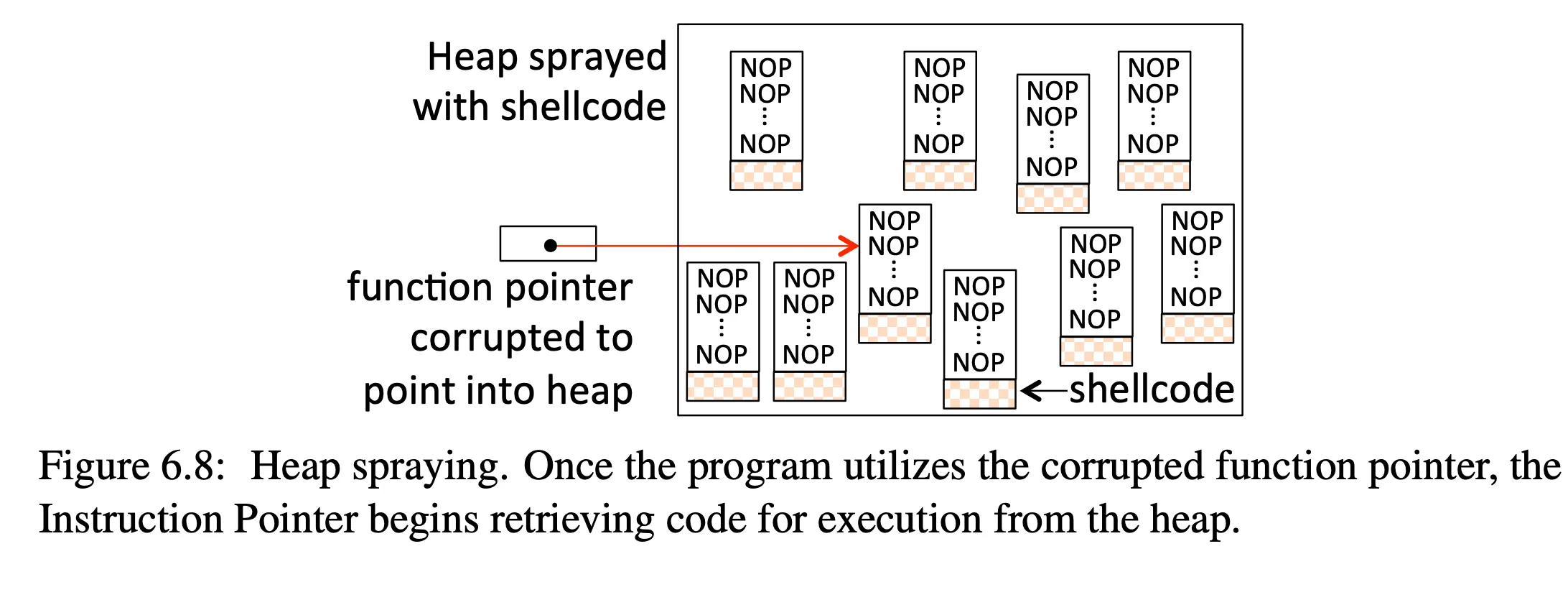
understand elements of a heap spraying attack — see Figure 6.8:
Class exercises
See the software security repo for code we will use:
- In
heap-overflowwe will runheapandheap2, which both have a heap overflow problem. In the first case we will try to change the role of a user, and in the second case we will try to change a function pointer. We’ll use theexploit.pyscript to help create the overflow and accomplish our goal.